Docker社から公式提供されているセキュリティツール。
CIS Docker Benchmarkに沿っているかが検証できる。
実行方法
docker/docker-bench-securityを参考にした。
# git clone https://github.com/docker/docker-bench-security.git
# cd docker-bench-security
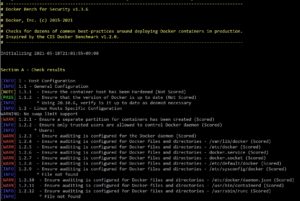
# ./docker-bench-security.sh
# --------------------------------------------------------------------------------------------
# Docker Bench for Security v1.3.6
#
# Docker, Inc. (c) 2015-2021
#
# Checks for dozens of common best-practices around deploying Docker containers in production.
# Inspired by the CIS Docker Benchmark v1.2.0.
# --------------------------------------------------------------------------------------------
Initializing 2021-05-18T21:01:55+09:00
Section A - Check results
[INFO] 1 - Host Configuration
[INFO] 1.1 - General Configuration
[NOTE] 1.1.1 - Ensure the container host has been Hardened (Not Scored)
[PASS] 1.1.2 - Ensure that the version of Docker is up to date (Not Scored)
[INFO] * Using 20.10.6, verify is it up to date as deemed necessary
[INFO] 1.2 - Linux Hosts Specific Configuration
WARNING: No swap limit support
[WARN] 1.2.1 - Ensure a separate partition for containers has been created (Scored)
[INFO] 1.2.2 - Ensure only trusted users are allowed to control Docker daemon (Scored)
[INFO] * Users:
[WARN] 1.2.3 - Ensure auditing is configured for the Docker daemon (Scored)
[WARN] 1.2.4 - Ensure auditing is configured for Docker files and directories - /var/lib/docker (Scored)
[WARN] 1.2.5 - Ensure auditing is configured for Docker files and directories - /etc/docker (Scored)
[WARN] 1.2.6 - Ensure auditing is configured for Docker files and directories - docker.service (Scored)
[WARN] 1.2.7 - Ensure auditing is configured for Docker files and directories - docker.socket (Scored)
[WARN] 1.2.8 - Ensure auditing is configured for Docker files and directories - /etc/default/docker (Scored)
[INFO] 1.2.9 - Ensure auditing is configured for Docker files and directories - /etc/sysconfig/docker (Scored)
[INFO] * File not found
[WARN] 1.2.10 - Ensure auditing is configured for Docker files and directories - /etc/docker/daemon.json (Scored)
[WARN] 1.2.11 - Ensure auditing is configured for Docker files and directories - /usr/bin/containerd (Scored)
[INFO] 1.2.12 - Ensure auditing is configured for Docker files and directories - /usr/sbin/runc (Scored)
[INFO] * File not found
[INFO] 2 - Docker daemon configuration
[WARN] 2.1 - Ensure network traffic is restricted between containers on the default bridge (Scored)
[PASS] 2.2 - Ensure the logging level is set to 'info' (Scored)
[PASS] 2.3 - Ensure Docker is allowed to make changes to iptables (Scored)
[PASS] 2.4 - Ensure insecure registries are not used (Scored)
[PASS] 2.5 - Ensure aufs storage driver is not used (Scored)
[INFO] 2.6 - Ensure TLS authentication for Docker daemon is configured (Scored)
[INFO] * Docker daemon not listening on TCP
[INFO] 2.7 - Ensure the default ulimit is configured appropriately (Not Scored)
[INFO] * Default ulimit doesn't appear to be set
[WARN] 2.8 - Enable user namespace support (Scored)
[PASS] 2.9 - Ensure the default cgroup usage has been confirmed (Scored)
[PASS] 2.10 - Ensure base device size is not changed until needed (Scored)
[WARN] 2.11 - Ensure that authorization for Docker client commands is enabled (Scored)
[WARN] 2.12 - Ensure centralized and remote logging is configured (Scored)
[WARN] 2.13 - Ensure live restore is enabled (Scored)
[WARN] 2.14 - Ensure Userland Proxy is Disabled (Scored)
[PASS] 2.15 - Ensure that a daemon-wide custom seccomp profile is applied if appropriate (Not Scored)
[INFO] Ensure that experimental features are not implemented in production (Scored) (Deprecated)
[WARN] 2.17 - Ensure containers are restricted from acquiring new privileges (Scored)
[INFO] 3 - Docker daemon configuration files
[PASS] 3.1 - Ensure that the docker.service file ownership is set to root:root (Scored)
[PASS] 3.2 - Ensure that docker.service file permissions are appropriately set (Scored)
[PASS] 3.3 - Ensure that docker.socket file ownership is set to root:root (Scored)
[PASS] 3.4 - Ensure that docker.socket file permissions are set to 644 or more restrictive (Scored)
[PASS] 3.5 - Ensure that the /etc/docker directory ownership is set to root:root (Scored)
[PASS] 3.6 - Ensure that /etc/docker directory permissions are set to 755 or more restrictively (Scored)
[INFO] 3.7 - Ensure that registry certificate file ownership is set to root:root (Scored)
[INFO] * Directory not found
[INFO] 3.8 - Ensure that registry certificate file permissions are set to 444 or more restrictively (Scored)
[INFO] * Directory not found
[INFO] 3.9 - Ensure that TLS CA certificate file ownership is set to root:root (Scored)
[INFO] * No TLS CA certificate found
[INFO] 3.10 - Ensure that TLS CA certificate file permissions are set to 444 or more restrictively (Scored)
[INFO] * No TLS CA certificate found
[INFO] 3.11 - Ensure that Docker server certificate file ownership is set to root:root (Scored)
[INFO] * No TLS Server certificate found
[INFO] 3.12 - Ensure that the Docker server certificate file permissions are set to 444 or more restrictively (Scored)
[INFO] * No TLS Server certificate found
[INFO] 3.13 - Ensure that the Docker server certificate key file ownership is set to root:root (Scored)
[INFO] * No TLS Key found
[INFO] 3.14 - Ensure that the Docker server certificate key file permissions are set to 400 (Scored)
[INFO] * No TLS Key found
[PASS] 3.15 - Ensure that the Docker socket file ownership is set to root:docker (Scored)
[PASS] 3.16 - Ensure that the Docker socket file permissions are set to 660 or more restrictively (Scored)
[PASS] 3.17 - Ensure that the daemon.json file ownership is set to root:root (Scored)
[PASS] 3.18 - Ensure that daemon.json file permissions are set to 644 or more restrictive (Scored)
[PASS] 3.19 - Ensure that the /etc/default/docker file ownership is set to root:root (Scored)
[INFO] 3.20 - Ensure that the /etc/sysconfig/docker file ownership is set to root:root (Scored)
[INFO] * File not found
[INFO] 3.21 - Ensure that the /etc/sysconfig/docker file permissions are set to 644 or more restrictively (Scored)
[INFO] * File not found
[PASS] 3.22 - Ensure that the /etc/default/docker file permissions are set to 644 or more restrictively (Scored)
[INFO] 4 - Container Images and Build File
[INFO] 4.1 - Ensure that a user for the container has been created (Scored)
[INFO] * No containers running
[NOTE] 4.2 - Ensure that containers use only trusted base images (Not Scored)
[NOTE] 4.3 - Ensure that unnecessary packages are not installed in the container (Not Scored)
[NOTE] 4.4 - Ensure images are scanned and rebuilt to include security patches (Not Scored)
[WARN] 4.5 - Ensure Content trust for Docker is Enabled (Scored)
[WARN] 4.6 - Ensure that HEALTHCHECK instructions have been added to container images (Scored)
[WARN] * No Healthcheck found: [nginx.slim:latest]
...
[INFO] 4.7 - Ensure update instructions are not used alone in the Dockerfile (Not Scored)
[INFO] * Update instruction found: [gcc:latest]
[INFO] * Update instruction found: [jenkins_jenkins:latest]
[INFO] * Update instruction found: [jenkins/jenkins:lts]
[INFO] * Update instruction found: [mysql:5.7]
[INFO] * Update instruction found: [wordpress:5.2]
[NOTE] 4.8 - Ensure setuid and setgid permissions are removed (Not Scored)
[INFO] 4.9 - Ensure that COPY is used instead of ADD in Dockerfiles (Not Scored)
[INFO] * ADD in image history: [nginx.slim:latest]
[NOTE] 4.10 - Ensure secrets are not stored in Dockerfiles (Not Scored)
[NOTE] 4.11 - Ensure only verified packages are are installed (Not Scored)
[INFO] 5 - Container Runtime
[INFO] * No containers running, skipping Section 5
[INFO] 6 - Docker Security Operations
[INFO] 6.1 - Ensure that image sprawl is avoided (Not Scored)
[INFO] * There are currently: 20 images
[INFO] 6.2 - Ensure that container sprawl is avoided (Not Scored)
[INFO] * There are currently a total of 73 containers, with only 0 of them currently running
[INFO] 7 - Docker Swarm Configuration
[PASS] 7.1 - Ensure swarm mode is not Enabled, if not needed (Scored)
[PASS] 7.2 - Ensure that the minimum number of manager nodes have been created in a swarm (Scored) (Swarm mode not enabled)
[PASS] 7.3 - Ensure that swarm services are bound to a specific host interface (Scored) (Swarm mode not enabled)
[PASS] 7.4 - Ensure that all Docker swarm overlay networks are encrypted (Scored)
[PASS] 7.5 - Ensure that Docker's secret management commands are used for managing secrets in a swarm cluster (Not Scored) (Swarm mode not enabled)
[PASS] 7.6 - Ensure that swarm manager is run in auto-lock mode (Scored) (Swarm mode not enabled)
[PASS] 7.7 - Ensure that the swarm manager auto-lock key is rotated periodically (Not Scored) (Swarm mode not enabled)
[PASS] 7.8 - Ensure that node certificates are rotated as appropriate (Not Scored) (Swarm mode not enabled)
[PASS] 7.9 - Ensure that CA certificates are rotated as appropriate (Not Scored) (Swarm mode not enabled)
[PASS] 7.10 - Ensure that management plane traffic is separated from data plane traffic (Not Scored) (Swarm mode not enabled)
[INFO] 8 - Docker Enterprise Configuration
[INFO] * Community Engine license, skipping section 8
Section B - Remediation measures
[INFO] 1 - Host Configuration
[INFO] 1.1.1 - You may consider various Security Benchmarks for your container host. Remediation Impact: None.
[INFO] 1.1.2 - You should monitor versions of Docker releases and make sure your software is updated as required. Remediation Impact: You should perform a risk assessment regarding Docker version updates and review how they may impact your operations.
[INFO] 1.2.1 - For new installations, you should create a separate partition for the /var/lib/docker mount point. For systems that have already been installed, you should use the Logical Volume Manager (LVM) within Linux to create a new partition. Remediation Impact: None.
[INFO] 1.2.2 - You should remove any untrusted users from the docker group using command sudo gpasswd -d <your-user> docker or add trusted users to the docker group using command sudo usermod -aG docker <your-user>. You should not create a mapping of sensitive directories from the host to container volumes. Remediation Impact: Only trust user are allow to build and execute containers as normal user.
[INFO] 1.2.3 - Install auditd. Add -w /usr/bin/dockerd -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart. Remediation Impact: Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions.
[INFO] 1.2.4 - Install auditd. Add -w /var/lib/docker -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart. Remediation Impact: Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions.
[INFO] 1.2.5 - Install auditd. Add -w /etc/docker -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart. Remediation Impact: Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions.
[INFO] 1.2.6 - Install auditd. Add -w /lib/systemd/system/docker.service -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart. Remediation Impact: Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions.
[INFO] 1.2.7 - Install auditd. Add -w /lib/systemd/system/docker.socket -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart. Remediation Impact: Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions.
[INFO] 1.2.8 - Install auditd. Add -w /etc/default/docker -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart. Remediation Impact: Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions.
[INFO] 1.2.9 - Install auditd. Add -w /etc/sysconfig/docker -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart. Remediation Impact: Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions.
[INFO] 1.2.10 - Install auditd. Add -w /etc/docker/daemon.json -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart. Remediation Impact: Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions.
[INFO] 1.2.11 - Install auditd. Add -w /usr/bin/containerd -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart. Remediation Impact: Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions.
[INFO] 1.2.12 - Install auditd. Add -w /usr/sbin/runc -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart. Remediation Impact: Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions.
[INFO] 2 - Docker daemon configuration
[INFO] 2.1 - Edit the Docker daemon configuration file to ensure that inter-container communication is disabled: icc: false. Remediation Impact: Inter-container communication is disabled on the default network bridge. If any communication between containers on the same host is desired, it needs to be explicitly defined using container linking or custom networks.
[INFO] 2.6 - Follow the steps mentioned in the Docker documentation or other references. By default, TLS authentication is not configured. Remediation Impact: You would need to manage and guard certificates and keys for the Docker daemon and Docker clients.
[INFO] 2.7 - Run Docker in daemon mode and pass --default-ulimit as option with respective ulimits as appropriate in your environment and in line with your security policy. Example: dockerd --default-ulimit nproc=1024:2048 --default-ulimit nofile=100:200 Remediation Impact: If ulimits are set incorrectly this could cause issues with system resources, possibly causing a denial of service condition.
[INFO] 2.8 - Please consult the Docker documentation for various ways in which this can be configured depending upon your requirements. The high-level steps are: Ensure that the files /etc/subuid and /etc/subgid exist. Start the docker daemon with --userns-remap flag. Remediation Impact: User namespace remapping is incompatible with a number of Docker features and also currently breaks some of its functionalities.
[INFO] 2.11 - Install/Create an authorization plugin. Configure the authorization policy as desired. Start the docker daemon using command dockerd --authorization-plugin=<PLUGIN_ID> Remediation Impact: Each Docker command needs to pass through the authorization plugin mechanism. This may have a performance impact
[INFO] 2.12 - Set up the desired log driver following its documentation. Start the docker daemon using that logging driver. Example: dockerd --log-driver=syslog --log-opt syslog-address=tcp://192.xxx.xxx.xxx Remediation Impact: None.
[INFO] 2.13 - Run Docker in daemon mode and pass --live-restore option. Remediation Impact: None.
[INFO] 2.14 - You should run the Docker daemon using command: dockerd --userland-proxy=false Remediation Impact: Some systems with older Linux kernels may not be able to support hairpin NAT and therefore require the userland proxy service. Also, some networking setups can be impacted by the removal of the userland proxy.
[INFO] 2.16 - You should not pass --experimental as a runtime parameter to the Docker daemon on production systems. Remediation Impact: None.
[INFO] 2.17 - You should run the Docker daemon using command: dockerd --no-new-privileges Remediation Impact: no_new_priv prevents LSMs such as SELinux from escalating the privileges of individual containers.
[INFO] 3 - Docker daemon configuration files
[INFO] 3.7 - You should run the following command: chown root:root /etc/docker/certs.d/<registry-name>/*. This would set the individual ownership and group ownership for the registry certificate files to root. Remediation Impact: None.
[INFO] 3.8 - You should run the following command: chmod 444 /etc/docker/certs.d/<registry-name>/*. This would set the permissions for the registry certificate files to 444. Remediation Impact: None.
[INFO] 3.9 - You should run the following command: chown root:root <path to TLS CA certificate file>. This sets the individual ownership and group ownership for the TLS CA certificate file to root. Remediation Impact: None.
[INFO] 3.10 - You should run the following command: chmod 444 <path to TLS CA certificate file>. This sets the file permissions on the TLS CA file to 444. Remediation Impact: None.
[INFO] 3.11 - You should run the following command: chown root:root <path to Docker server certificate file>. This sets the individual ownership and the group ownership for the Docker server certificate file to root. Remediation Impact: None.
[INFO] 3.12 - You should run the following command: chmod 444 <path to Docker server certificate file>. This sets the file permissions of the Docker server certificate file to 444. Remediation Impact: None.
[INFO] 3.13 - You should run the following command: chown root:root <path to Docker server certificate key file>. This sets the individual ownership and group ownership for the Docker server certificate key file to root. Remediation Impact: None.
[INFO] 3.14 - You should run the following command: chmod 400 <path to Docker server certificate key file>. This sets the Docker server certificate key file permissions to 400. Remediation Impact: None.
[INFO] 3.20 - You should run the following command: chown root:root /etc/sysconfig/docker. This sets the ownership and group ownership for the file to root. Remediation Impact: None.
[INFO] 3.21 - You should run the following command: chmod 644 /etc/sysconfig/docker. This sets the file permissions for this file to 644. Remediation Impact: None.
[INFO] 4 - Container Images and Build File
[INFO] 4.1 - You should ensure that the Dockerfile for each container image contains the information: USER <username or ID>. If there is no specific user created in the container base image, then make use of the useradd command to add a specific user before the USER instruction in the Dockerfile. Remediation Impact: Running as a non-root user can present challenges where you wish to bind mount volumes from the underlying host. In this case, care should be taken to ensure that the user running the contained process can read and write to the bound directory, according to their requirements.
[INFO] 4.2 - Configure and use Docker Content trust. View the history of each Docker image to evaluate its risk, dependent on the sensitivity of the application you wish to deploy using it. Scan Docker images for vulnerabilities at regular intervals. Remediation Impact: None.
[INFO] 4.3 - You should not install anything within the container that is not required. You should consider using a minimal base image if you can. Some of the options available include BusyBox and Alpine. Not only can this trim your image size considerably, but there would also be fewer pieces of software which could contain vectors for attack. Remediation Impact: None.
[INFO] 4.4 - Images should be re-built ensuring that the latest version of the base images are used, to keep the operating system patch level at an appropriate level. Once the images have been re-built, containers should be re-started making use of the updated images. Remediation Impact: None.
[INFO] 4.5 - Add DOCKER_CONTENT_TRUST variable to the /etc/environment file using command echo DOCKER_CONTENT_TRUST=1 | sudo tee -a /etc/environment. Remediation Impact: This prevents users from working with tagged images unless they contain a signature.
[INFO] 4.6 - You should follow the Docker documentation and rebuild your container images to include the HEALTHCHECK instruction. Remediation Impact: None.
[INFO] 4.7 - You should use update instructions together with install instructions and version pinning for packages while installing them. This prevent caching and force the extraction of the required versions. Alternatively, you could use the --no-cache flag during the docker build process to avoid using cached layers. Remediation Impact: None.
[INFO] 4.8 - You should allow setuid and setgid permissions only on executables which require them. You could remove these permissions at build time by adding the following command in your Dockerfile, preferably towards the end of the Dockerfile: RUN find / -perm /6000 -type f -exec chmod a-s {} ; || true Remediation Impact: The above command would break all executables that depend on setuid or setgid permissions including legitimate ones. You should therefore be careful to modify the command to suit your requirements so that it does not reduce the permissions of legitimate programs excessively. Because of this, you should exercise a degree of caution and examine all processes carefully before making this type of modification in order to avoid outages.
[INFO] 4.9 - You should use COPY rather than ADD instructions in Dockerfiles. Remediation Impact: Care needs to be taken in implementing this control if the application requires functionality that is part of the ADD instruction, for example, if you need to retrieve files from remote URLS.
[INFO] 4.10 - Do not store any kind of secrets within Dockerfiles. Where secrets are required during the build process, make use of a secrets management tool, such as the buildkit builder included with Docker. Remediation Impact: A proper secrets management process will be required for Docker image building.
[INFO] 4.11 - You should use a secure package distribution mechanism of your choice to ensure the authenticity of software packages. Remediation Impact: None.
[INFO] 6 - Docker Security Operations
[INFO] 6.1 - You should keep only the images that you actually need and establish a workflow to remove old or stale images from the host. Additionally, you should use features such as pull-by-digest to get specific images from the registry. Remediation Impact: docker system prune -a removes all exited containers as well as all images and volumes that are not referenced by running containers, including for UCP and DTR.
[INFO] 6.2 - You should periodically check your container inventory on each host and clean up containers which are not in active use with the command: docker container prune Remediation Impact: You should retain containers that are actively in use, and delete ones which are no longer needed.
Section C - Score
[INFO] Checks: 76
[INFO] Score: 5
auditdの設定後に実行した
[Section B – Remediation measures]にしたがってauditdをインストールしてみた。
# apt install auditd # vi /etc/audit/rules.d/audit.rules -w /usr/bin/dockerd -k docker -w /usr/bin/docker -k docker -w /var/lib/docker -k docker -w /etc/docker -k docker -w /lib/systemd/system/docker.service -k docker -w /lib/systemd/system/docker.socket -k docker -w /etc/default/docker -k docker -w /etc/docker/daemon.json -k docker -w /usr/bin/containerd -k docker -w /usr/sbin/runc -k docker # systemctl restart auditd
点数が上がっていることが確認できた。
# ./docker-bench-security.sh ... [INFO] Checks: 76 [INFO] Score: 17